CCIE SECURITY GNS3
January 30, 2013 26 Comments
WordPress Blog https://ccie4all.wordpress.com/ information about the changes made to Gns3 BGP , MPLS and R&S CCIE labs.
In order to access and download all provided materials and receive important updates from above posts under GNS3 tab in the main header please go ahead and subscribe to https://ccie4all.wordpress.com/ !
All other posts have not been affected and can be accessed at any given time.
Hi All !
Just like with R&S , MPLS and BGP set ups this post is dedicated to the best practise for setting up CCIE SECURITY lab in GNS3 and I want to show you how to set up a practise rack!
Below you will find initial CCIE Security configs for the following topologies/series (IPExpert and Netmetric initial configs will become available at a later date):
————————————————————————————————————————————————————————-
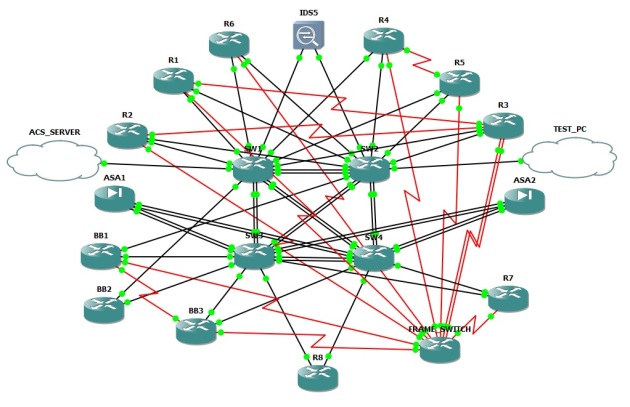
CCBootcamp Security – see below image
CCBootcamp Initial Configs : R1cc R2cc R3cc R4cc R5cc R6cc R7cc R8cc
SW1cc SW2cc SW3cc SW4cc Frame_switchcc
Frame_switchcc IDScc BB1cc BB2cc ASA1cc ASA2cc
————————————————————————————————————————————————————————-
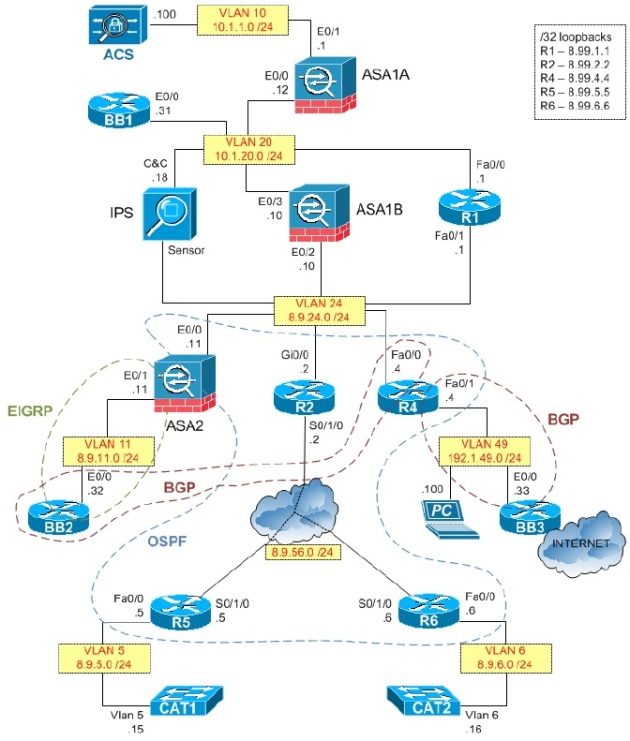
INE Security – see below image and initial configs (I have decided to use different topology for INE as the previous one only had one Backbone router and it’s way more fun with more)
INE Initial configs : R1 R2 R3 R4 R5 R6 SW1 SW2 SW3 SW4
IDS FRAME_SWITCH BB1 BB2 BB3 ASA1 ASA2
————————————————————————————————————————————————————————-
IPExpert Security – see below image
————————————————————————————————————————————————————————-
Netmetric – see below image :
I have spent number of long hours to prepare above GNS3 topology to make it work with almost any lab scenario you can find on the internet and I believe it is ready to go. I will soon attach a GNS3.NET.FILE so you will be able to build it in exact same way on your PC. As you know from my previous posts about R&S , BGP and MPLS GNS3 topologies it is crucial to connect all devices in exact same way as it is specified in the GNS3.NET.FILE as otherwise the set up will not work efficiently then when you launch it you will be able to copy and paste provided initial configs (basic routing protocols , ip address , vlans etc…) into every devices and start labbing.
GNS3 NET FILE : NET FILE
VLANS : VLANS
There’s not a lot of switching in security. Vlans doc contains all vlans that you will need despite what series you’re going through , so simple paste those into switches at the very beginning then use all the remaining configs.
In order to fully run this GNS3 CCIE Security network on your machine you must have :
1. Use a high-end system with good processor and plenty of RAM, preferably 8GB or more also close programs and Windows services that you don’t use before running GNS3, this way, you can save (precious) CPU and RAM usage
2. Use latest IOS versions (at least to support new commands and features) and configure your routers to use the correct RAM requirements by checking their documentation from Cisco website. My router’s IOS requires at least 128MB and when I don’t change the default of 64MB, it still runs but it always crashes after some time
3. When running / starting your topology, I recommend running the devices one at a time. But on the first router of each model (if you use different models in a topology), after running it, configure and select idle/pc that uses low CPU. I always open Task Manager when using GNS3 so I can monitor the CPU and RAM usage.
4. ASA must have asa842 (5520) GNS3 image on it
5. IDS must have IDS\IPS Qemu\IPS Qemu GNS3 image on it
6. VMware with Windows XP or Professional (TEST PC)
7. AAA windows licence which you run on another VM machine (AAA_SERVER)
ISSUES PINGING SVI INTERFACES ON THE SWITCHES
I’ve been dealing with this issue all day today. In my case, the issue was that if I have TWO of the NM-16ESW cards installed into a 37xx router, back-to-back L3 links with IP addresses work fine but I cannot ping SVIs on the switch.
For example:
Router6 (f0/0) -> SW2 (f1/6)
If Router6’s interface has an IP address assigned and SW2’s interface has an IP address assigned, everything works great with two cards installed.
However, if Router6 has an IP address assigned (or subinterfaces) and SW2 is an access port on VLAN 1, the SVI for VLAN 1 on SW2 cannot be pinged. CDP still shows the connection up, but pings do not get through.
Note that this issue will occur even if all your connections are on the first slot’s NM-16ESW module — the second one just needs to be present in order to break things. Removing the second NM-16ESW module from my SW2 router fixed all my issues , looks like a GNS3 internal bug.
TEST PC & IPS
As you can see a TEST_PC is not included in every topology however from my experience it is definitely good practise to have one and you wll most definitely need one when configuring IPS appliance(see below). Simply attach one of your Microsoft loopbacks adapter to the TEST_PC cloud , assign relevant to the series that you’re watching ip address to it and allow it on the trunk
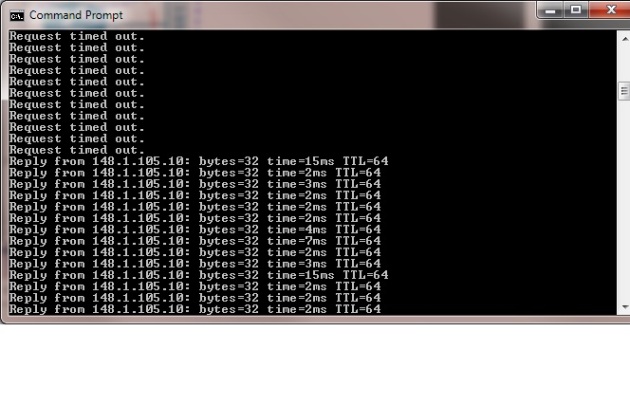
You should be able to ping and connect to the IPS from your physical machine on port 443 from your browser , see below output from my PC:
Caution ! This set up will crash your PC therefore please remember that it is crucial to make sure that you have a super fast processor and enough ram but once you’ve got it all it works perfectly !
This post will be publicly open until all configs files have been uploaded and after that it will be available to the subscribed members only so please go ahead and subscribe !
Enjoy !
Tom




Recent Comments